People
- Professor Klara Nahrstedt: Principle Investigator
- Hoang Nguyen: Ph.D. candidate
- Qiyan Wang: Ph.D. candidate
- Raoul Vicente Rivas Toledano: Ph.D. candidate
- Hongyang Li: Ph.D. candidate
Projects
- Alibi: Identify Insider-Based Jamming Attacks
- iDSRT: Integrated Dynamic Soft Real-time Architecture
- Time-Critical Multicast Authentication
- ACF: Attack Containment Framework
Publication
- Gyorgy Dan, King-Shan Lui, Rehana Tabassum, Quanyan Zhu, Klara Nahrstedt, “SELINDA: A Secure, Scalable and Light-Weight Data Collection Protocol for Smart Grids”, IEEE SmartGridComm 2013, “Smart Grid Cyber Security and Privacy” Symposium, Vancouver, Canada, October 21-24, 2013.
- Haiming Jin, King-Shan Lui, Suleyman Uludag, Klara Nahrstedt, “ Secure Data Collection in Constrained Tree-Based Smart Grid Environments”, IEEE SmartGridComm’14 Symposium– Communications and Networks Track, Italy, 2014
- Suleyman Uludag, King-Shan Lui, Wenyu Ren, Klara Nahrstedt, “Practical and Secure Machine-to-Machine Data Collection Protocol in Smart Grid”, Workshop on Security and Privacy in Machine-to-Machine Communications (M2MSec’14), 2014
- Suleyman Uludag, King-Shan Lui, Wenyu Ren, Klara Nahrstedt, “Secure and Scalable Data Collection with Time Minimization in the Smart Grid,”, IEEE Transactions on Smart Grid, Vol. 7, No. 1, January 2016
- Hongpeng Guo, King-Shan Lui, Tianyuan Liu, Klara Nahrstedt, “Resilient Collection Protocol for Oil and Gas Refinery Network with In-node Processing”, IEEE ICNC (International Conference on Computing, Networking and Communications), CNC (International Workshop on Computing, Networking and Communications) 2018, Maui, Hawaii, March 2018.
- Qiyan Wang, Himanshu Khurana, Ying Huang, and Klara Nahrstedt,“Time Valid One-Time Signature for Time-Criticial Multicast Data Authentication”, 28th Annual IEEE Conference on Computer Communications (INFOCOM) , 2009.
- Hoang Nguyen, Raoul Rivas, Klara Nahrstedt, iDSRT: Integrated Dynamic Soft Real-time Architecture for Critical Infrastructure Data Delivery over WLAN, The Sixth International ICST Conference on Heterogeneous Networking for Quality, Reliability, Security and Robustness (QShine), 2009
- Hoang Nguyen, Thadpong Pongthawornkamol and Klara Nahrstedt, A novel approach to identify insider-based jamming attacks in multi-channel wireless networks, Proc. of Military Communications Conference (MILCOM), 2009
- Hoang Nguyen, Klara Nahrstedt, Attack Containment Frame for Large-Scale Critical Infrastructures, 16th International Conference on Computer Communications and Networks (ICCCN), 2007
- Wenbo He, Xue Liu, Hoang Nguyen, Klara Nahrstedt, Tarek Abdelzaher, PDA: Privacy-preserving Data Aggregation in Wireless Sensor Networks, 26th Annual IEEE Conference on Computer Communications (INFOCOM), 2007
- Wenbo He, Ying Huang, Klara Nahrstedt, Whay C. Lee, SMOCK: A Self-contained Public Key Management Scheme for Mission-critical Wireless Ad Hoc Networks, in Proc. of 5th Annual IEEE International Conference on Pervasive Computing and Communications (PerCom), 2007
- Hoang Nguyen, Klara Nahrstedt, Detecting Anomalies by Data Aggregation in the Power Grid, UIUC Tech. Report, 2006
Project description
Alibi: Identify Insider-Based Jamming Attacks
We consider the problem of detecting the insider-based attacks in the form of jammers in a single-hop wireless LAN environment, where jammers have the inside knowledge of frequency hopping patterns and any protocols used in the wireless network. We propose a novel jammer model in which the jammers are modeled by the number of channels that they can jam simultaneously. We further propose the novel concept of an atomic jammer which is the basic component necessary to deal with stronger jammers. To deal with atomic jammers, we propose a class of novel protocols called alibi protocols. The basic idea of the alibi protocols is to exploit one major limitation of the atomic jammers: they cannot jam two channels at the same time. Therefore, honest nodes in the network can occasionally switch to another channel, called the alibi channel, to transmit proofs for their honesty witnessed by some other honest nodes. We specify a necessary condition and desired properties such as detection time, false alarms and miss detections of this class of protocols. We prove that with high probability the detection time of these protocols is O(n ln(n)). We also propose some more practical alibi-based protocols such as 1-propagation and 1-gossiping and prove their desired properties. We further extend our work to the lossy channel model. The simulation results in ns2 confirm our analysis. The overall results of these protocols show a promising research direction to deal with insider-based jamming attacks.
iDSRT: Integrated Dynamic Soft Real-time Architecture
a system providing application-to-application delay guarantee over wireless networks. iDSRT employs a Dynamic Soft Real-time CPU scheduler (DSRT) and Implicit Earliest Deadline First Network Scheduler (iEDF) in an integrated manner to provide a true end-to-end delay guarantee, i.e. both operating system delay guarantee and network delay guarantee. We implemented iDSRT in Linux kernel 2.6.20 and evaluated it under a test bed of 7 nodes equipped with 802.11a/b/g wireless cards. The experiments show iDSRT can guarantee the delay correctly and has extremely low packet loss under a heavy load of traffic compared to other schemes over 802.11. (the first version of iDSRT distributed to Washington State University under the academic license. The current version is sponsored by Department of Energy ).
Time-Critical Multicast Authentication
Multicast authentication is a security primitive that enables each receiver in the multicast group to verify if received data originates from the claimed sender and was not altered on the way. This work is motivated by the need for authenticating time-critical multicast data in the power grid, which is one of the largest cyber-physical critical infrastructures and is being transformed today with the design and development of advanced real-time control applications. These applications aim to allow timely control of power flow over physical power networks based on data from monitoring and control devices such as PMUs (Phasor Measurement Units) and relays.
It is challenging to provide authentication to time-critical multicast data, where low end-to-end delay is of crucial importance. Consequently, it requires not only efficient authentication algorithms to minimize computational cost, but also avoidance of buffering packets. In this work, we propose a novel signature model – Time Valid One-Time Signature (TV-OTS) – to boost the efficiency of regular one-time signature schemes. Based on the TV-OTS model, we design an efficient multicast authentication scheme “TV-HORS”, which combines one-way hash chains with TV-OTS to avoid frequent public key distribution. TV-HORS provides fast signing/verification and buffering-free data processing, and has perfect tolerance to packet loss and strong robustness against malicious attacks. In addition, TV-HORS has smaller signature size compared with other signature schemes.
ACF: Attach Containment Framework
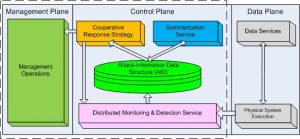
As the Power Grid is a large-scale system of variety of nodes with large amount of time-sensitive data and lack of processing capabilities, aggregation of data and resources becomes a potential approach for intrusion detection and attack containment. We propose an attack containment framework (ACF) which is a integration of early warning and cooperative response approach. The framework lies in the novel concept of attack container which is an information structure and captures the trust behavior of a group and assists to contain the damage of the attacks.
We are currently looking at the value-changing attacks which essentially comes from the threat of software/firmware updates of Intelligent Electronic Devices (IED) by the vendors. However, we are not limiting ourselves to this type of attacks. The next step we are taking is timing attacks such as Denial-of-Service (DoS) attacks. We will also look at other type of attacks such as slander attack, sybil attack. The ultimate goal is to design the framework that can mitigate and contain these attacks.
The ACF framework enables different degrees of containment. Coarse-grained (hard) containment (i.e. containment in previous work) applies expensive and maybe slow actions to contain possible attacks. Typical examples of these actions are changing firewall policies, blocking accesses.Fine-grained (soft) containment happens much earlier than coarse-grained containment. Its goal is to apply much cheaper and softer actions to limit attackers’ capabilities and to drive the system out of the critical state. We are currently investigating these actions. Please come back and check out this exciting research.
The ACF framework also integrates other preventive schemes such as key management issues.
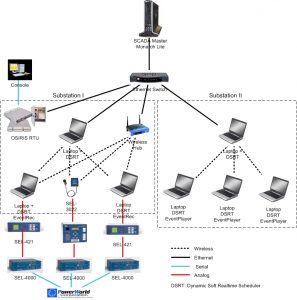
Testbed: We evaluate our framework by both analysis and testbed. The testbed consists of real power devices and emulated devices.
Funding Agencies
This project is a part of NSF TCIPG project at UIUC. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Science Foundation or US government.
